Critical Nodes - Watson Project
Fraud vulnerability assessment in representative European agri-food supply chains
To add a comment, click on the "+" next to the relevant sentence / paragraph. The first time you comment, you will be prompted to create a profile with name and email address. Kindly note that your chosen name will be displayed with your comments, and it cannot be changed without deleting the comment. The email address will not be displayed publicly, but it will be available to project partners. For further details please see the privacy policy.
1. Introduction of Watson Project
Watson is an €11 million 3-year project with 45 partners across 20 countries funded by the European Union’s (EU) research and innovation framework Horizon Europe. The main goal of Watson is to combat fraudulent practices in the food chain by integrating various digital technological solutions that can be applied effectively across multiple agri-food supply chains. The proposed framework will be tested in 7 agri-food supply chains across different European countries considering different operational procedures and diverse environments: cereal, dairy, fish, honey, meat, olive oil, and wine. To achieve this, numerous digital technologies and platforms, such as portable DNA-based devices, multi-sensor scanning devices, IoT platforms, blockchain platforms, mobile apps, and digital product passports, will be used at different supply chain stages to prevent food fraud. Additionally, an early warning system based on robust and explainable artificial intelligence will be established in this food fraud prevention framework. This project will emphasize the need to enhance fraud prevention systems and validate the solutions in specific agri-food chains. The project will also contribute to raising consumer awareness regarding food safety and fraud, ultimately leading to the adoption of healthier lifestyles and the development of sustainable food ecosystems. The aim is to improve the integrity, authenticity, and safety of the global food supply chain, protect consumers, and foster trust in the food industry. Further information can be found on the Watson website.sentence permalink
2. Introduction of Food Fraud Vulnerability Assessment
Food fraud vulnerability assessments of the representative EU food supply chains is essential to the Watson project. A food fraud vulnerability assessment aims to investigate and analyze potential vulnerabilities and underlying reasons for integrity issues in food supply chains. The evaluation involves collaboration from various stakeholders from across the supply chain to identify and analyze the most vulnerable nodes in potential fraud activities (Manning & Soon, 2019). The goal is to delve into the root drivers of food fraud, including opportunities, motivational drivers, and lack of controls. The findings will contribute to developing comprehensive guidelines to overcome systemic enablers and barriers to implementing innovative solutions.sentence permalink
3. Methodology
3.1 Adaption of the SSAFE FFAV tool to the EU food supply chain
Food fraud vulnerability assessment collects and evaluates information on potential food fraud risk factors and mitigation measures that determine the actual fraud vulnerability.sentence permalink
A practical food fraud vulnerability assessment tool (FFAV) was developed previously (Ruth, 2019).sentence permalink
The original version contains 50 questions covering the fraud opportunity, motivations, and control measures.sentence permalink
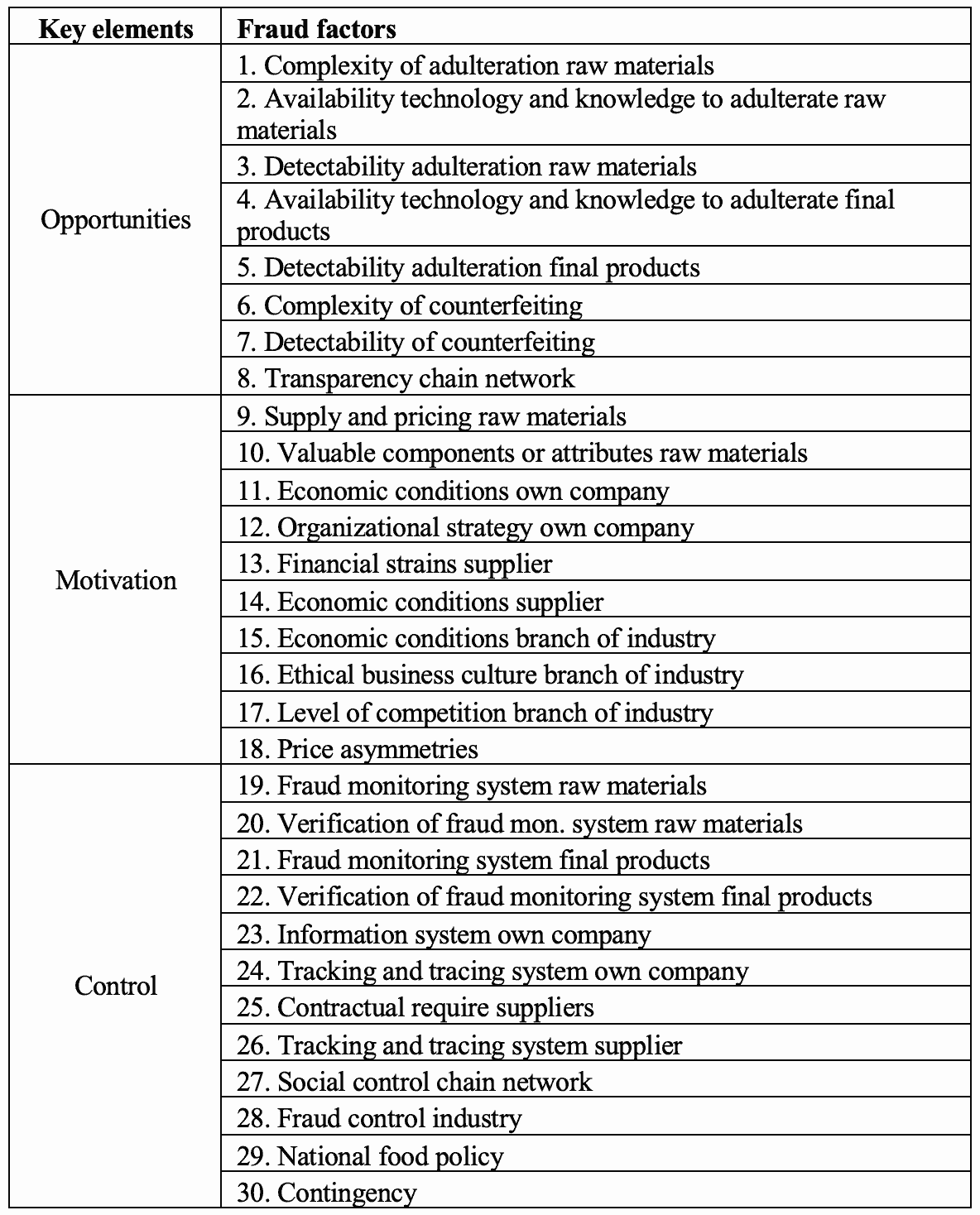
Table 1. The key elements in food fraud vulnerability assessment and 30 related fraud factors included in the Watson FFAV questionnaire.sentence permalink
The FFAV tool was adapted to the participating supply chains in the Watson project, and 30 relevant questions were selected and compiled in a questionnaire.sentence permalink
Each question related to the identified fraud factors: 8 for opportunities, 10 for motivations, and 12 for control measures (Table 1).sentence permalink
3.2 Workshop and questionnaire methodology
This investigation and analysis of the vulnerabilities and root drivers of integrity issues within the 7 agri-food supply chains was done through workshops in each chain with 15-20 stakeholders.sentence permalink
A workshop is an organized and interactive event that enables participants to learn and collaborate on a specific topic, skill, or problem.sentence permalink
They typically involve a combination of presentations, discussions, group activities, and exercises to gather information and perspectives from stakeholders.sentence permalink
The Watson workshops involved collaborative discussions between groups of participants representing each supply chain, including third-party controllers.sentence permalink
The main objective of these workshops is to identify the most vulnerable nodes in each chain where fraud is most likely to occur.sentence permalink
During the workshops for each chain, the basic concepts of food fraud and food fraud vulnerability assessment were first introduced.sentence permalink
Instructions on the application of the FFAV tool were then given to all the participants during the workshop.sentence permalink
All the participants were suggested to answer the FFAV questionnaire according to their experiences and expertise while working in their supply chain.sentence permalink
To ensure a wider collection of results and involve those stakeholders who could not participate in workshops, the Watson FFAV questionnaire was made available online.sentence permalink
Watson partners circulated this questionnaire to relevant supply chain stakeholders in their network.sentence permalink
The results from both the workshops and online questionnaires are compiled in this analysis.sentence permalink
3.3 Research participants
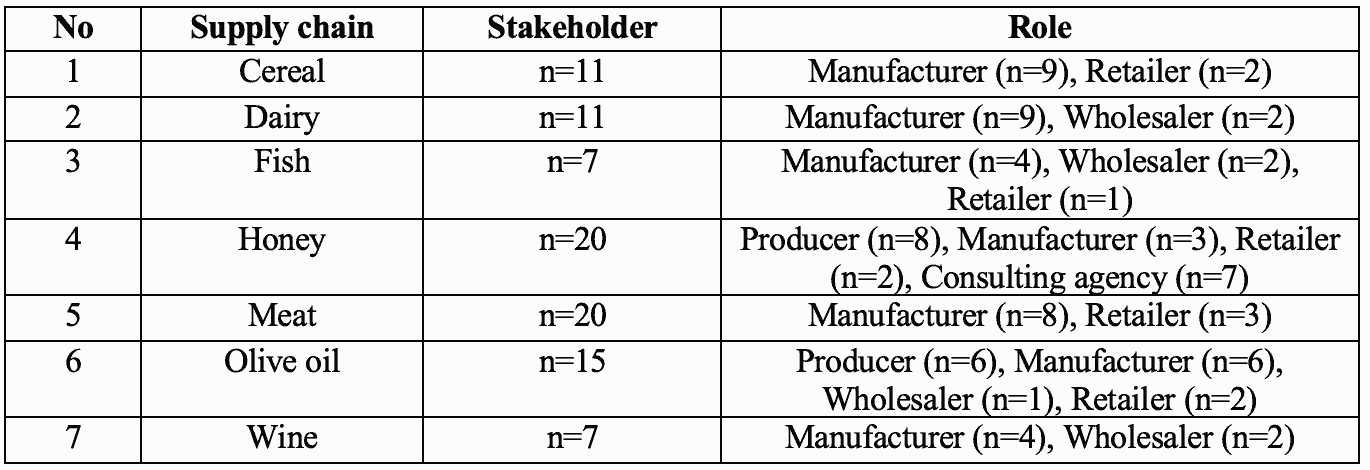
Seven representative EU food supply chains, including cereal, dairy, fish, honey, meat, olive oil, and wine, were included in this food fraud vulnerability assessment.sentence permalink
A total of 81 stakeholders in the above supply chains with different roles were assessed using the adopted FFAV tools through workshops and questionnaires.sentence permalink
The details regarding the numbers and roles of stakeholders are summarized in Table 2.sentence permalink
3.4 Data analysis
The FFAV tool uses a scoring system that assigns a score of 1, 2, or 3 to low, medium, and high vulnerability situations for opportunities and motivations.sentence permalink
For control measures, a score of 1, 2, or 3 is assigned to high, medium, and low vulnerability situations.sentence permalink
The first step is to calculate these three types of frequencies for the seven supply chains.sentence permalink
Then, the frequency of perceived vulnerability levels for each key element is determined using the following formula:sentence permalink
Fi = Sij/Gjsentence permalink
The Fi is the frequency of the vulnerability score i (i = 1, 2, 3), Sij is the number of observations that get score i in the following group j (j means the key elements of food fraud vulnerability), Gj is the total number of observations in groups (Yan et al., 2020).sentence permalink
4. Results and Discussion
4.1. General results of food fraud vulnerability across all supply chains
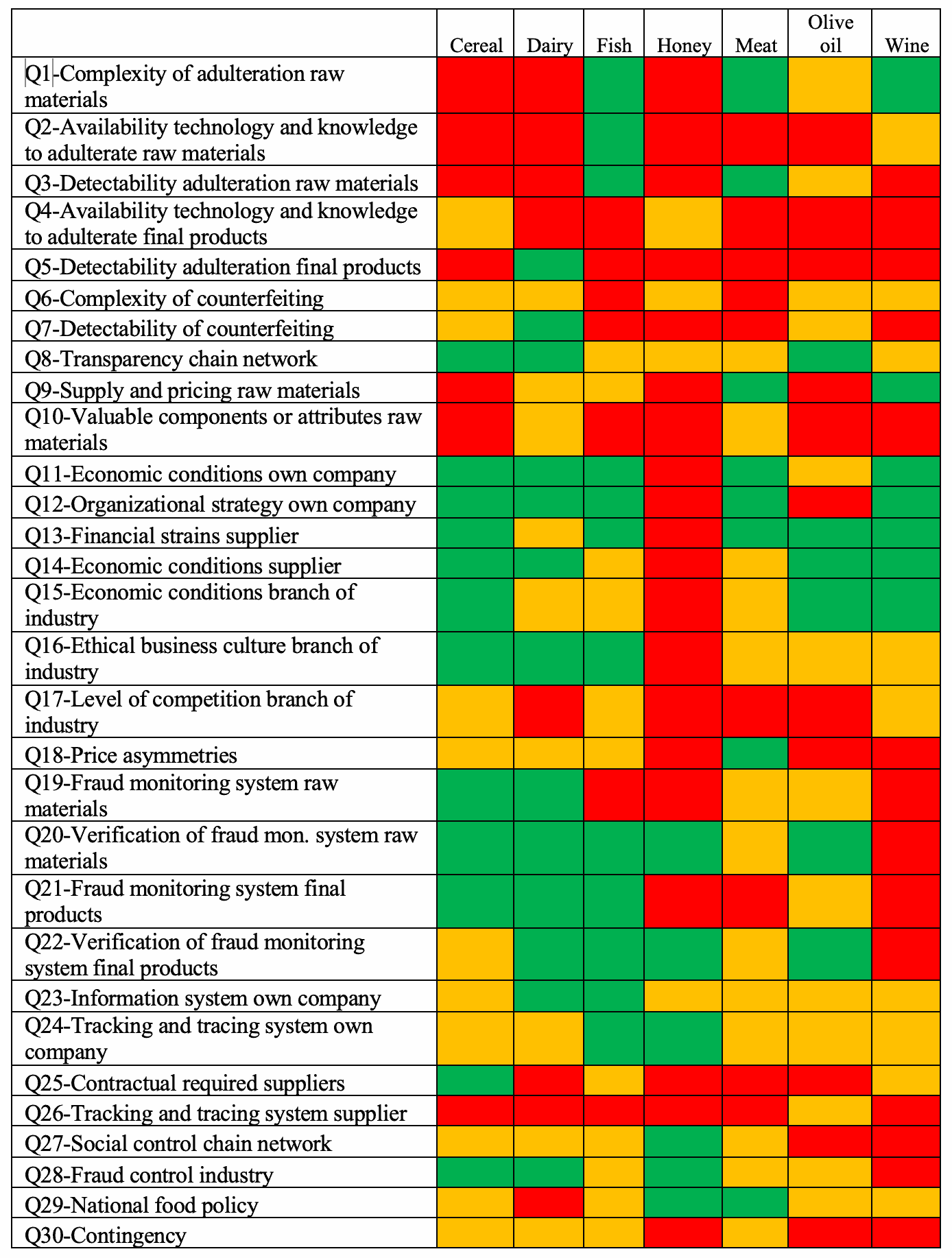
Table 3 displays each question's most commonly selected vulnerability levels, providing an initial view of differences and similarities across commodity supply chains.sentence permalink
Table 3. Tiling visualization of frequently recorded fraud vulnerability scores (modes) for each fraud factor across seven selected commodity supply chains. Modes colored based on vulnerability: red for high, orange for medium, and green for low.sentence permalink
Overall, opportunities received higher scores than motivations and control measures.sentence permalink
The honey, olive oil, and wine supply chains had the most highly vulnerable markers.sentence permalink
The main economic motivations rely on the valuable components of products, the competition level and the price variation in geographical distribution. In the meantime, the fraud risk in control measures is generally less than the opportunity and motivation.sentence permalink
The main fraud factors were reported as follows: Q19-Fraud monitoring system raw materials, Q21-Fraud monitoring system final products, Q25-Contractual requirements for suppliers, Q26-Tracking and tracing system supplier, and Q30-Contingency.sentence permalink
Our results show that all supply chains participating in the survey generally lack food fraud detection systems for raw materials and final products.sentence permalink
This indicates that in practical applications, there is an urgent need to propose a systematic food fraud detection system to help the industry better protect the integrity of the supply chain.sentence permalink
Food traceability systems are vulnerable, which is worrisome for both processing companies and sellers.sentence permalink
To ensure food safety, it is crucial to have reliable traceability systems that cover the entire industry chain.sentence permalink
Our findings reveal that the absence of a universal and trustworthy traceability system is a significant factor contributing to the current food insecurity.sentence permalink
4.2 The comparison of fraud vulnerability in the different supply chains
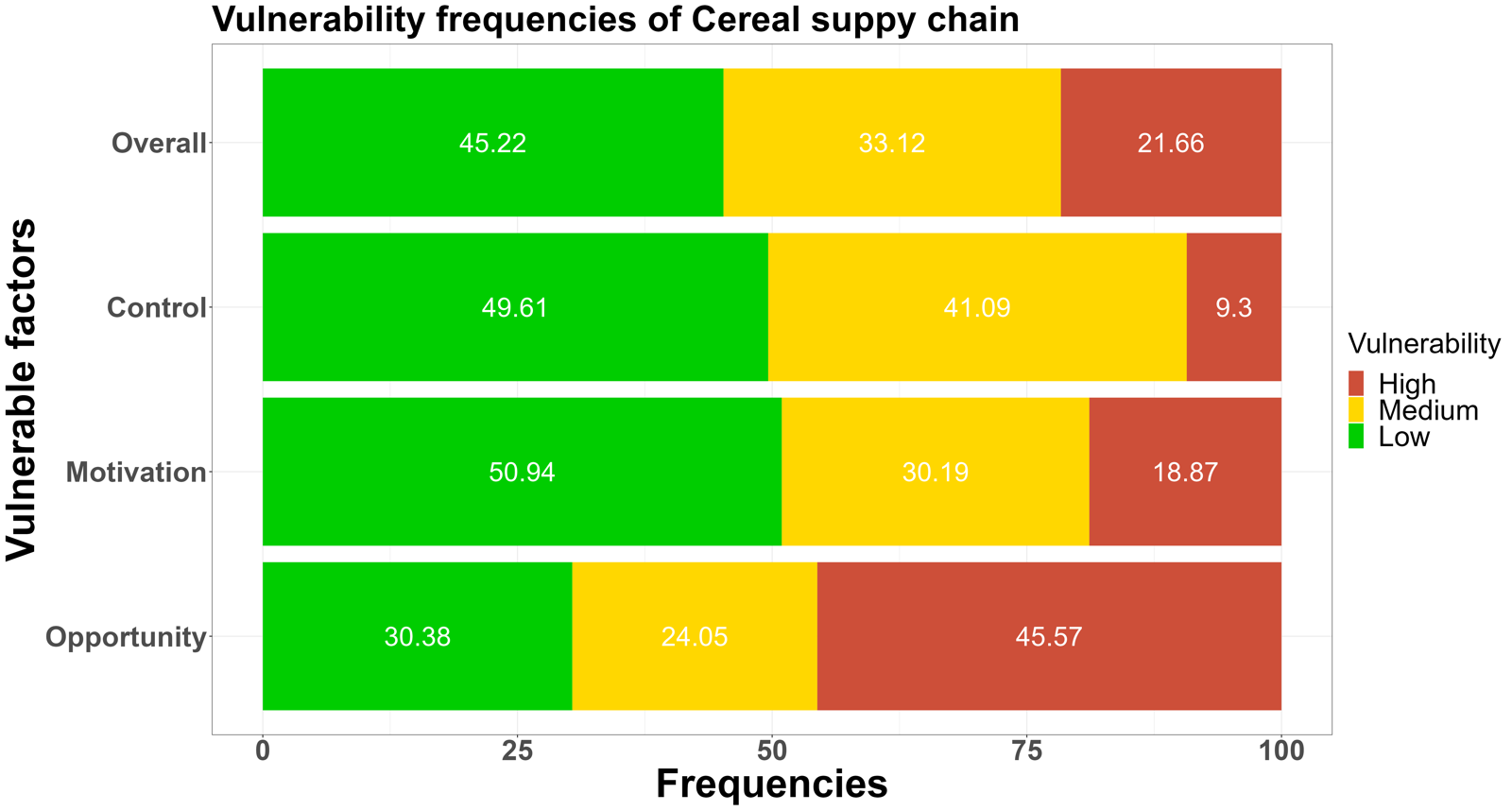
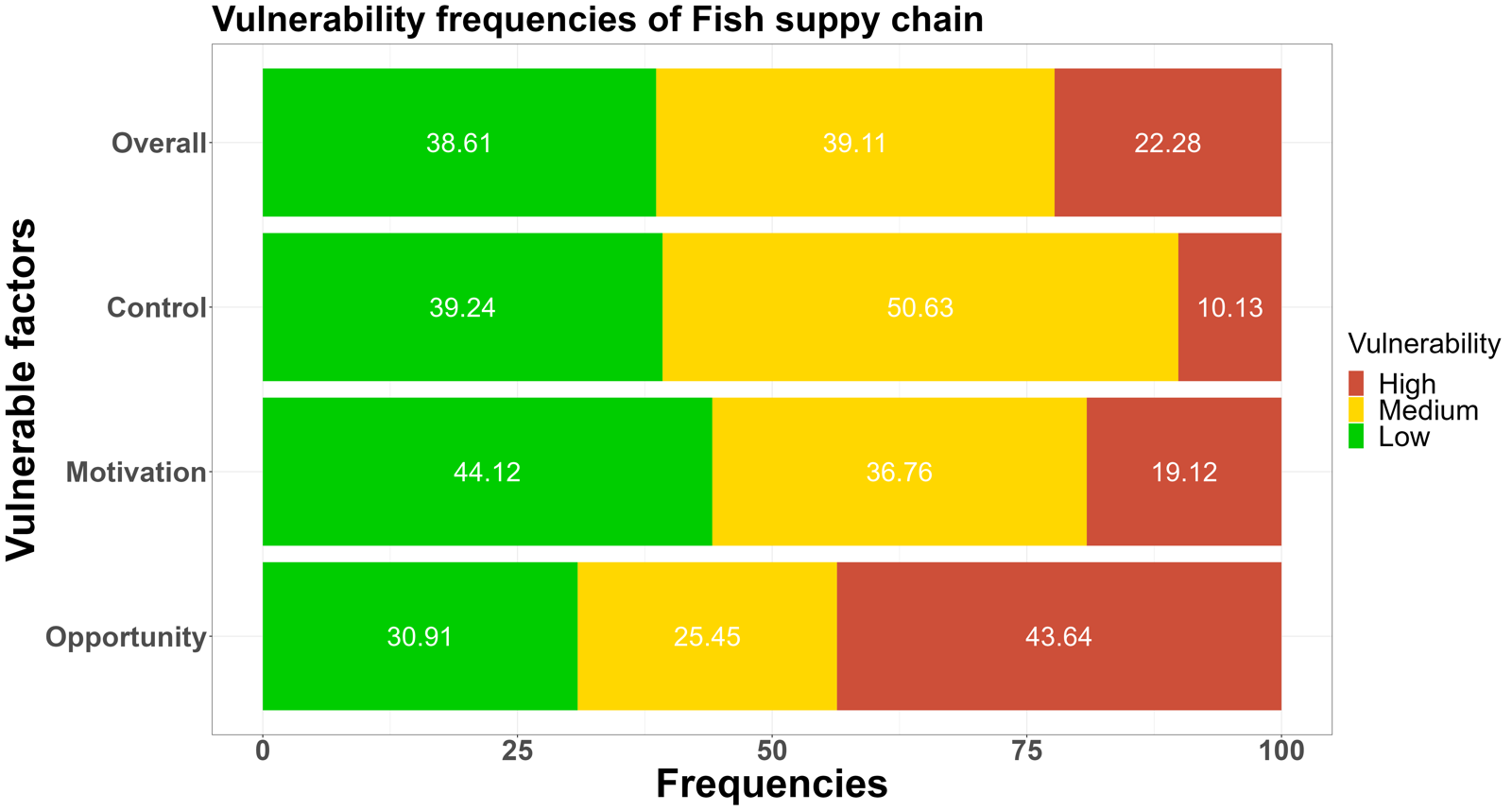
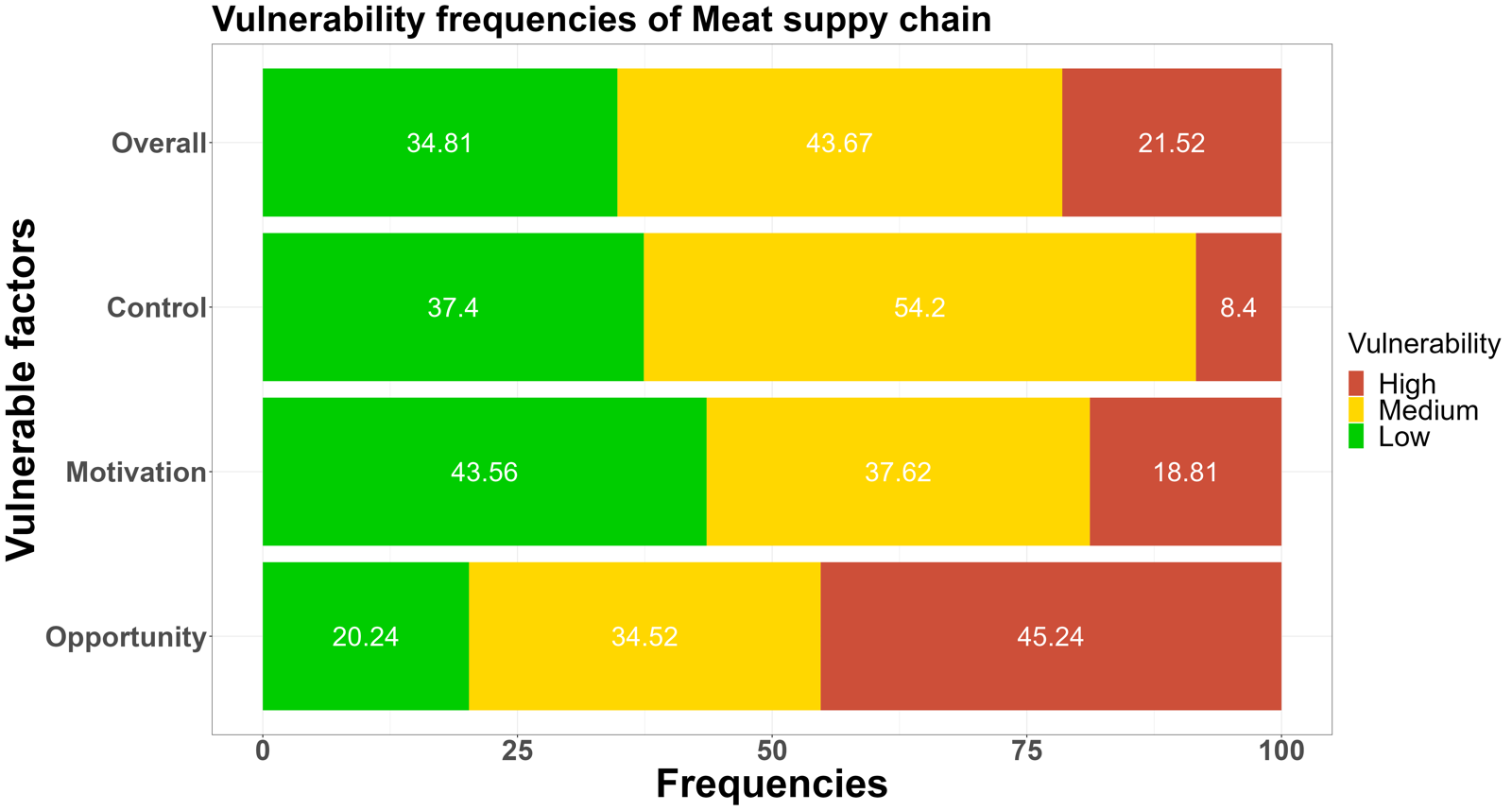
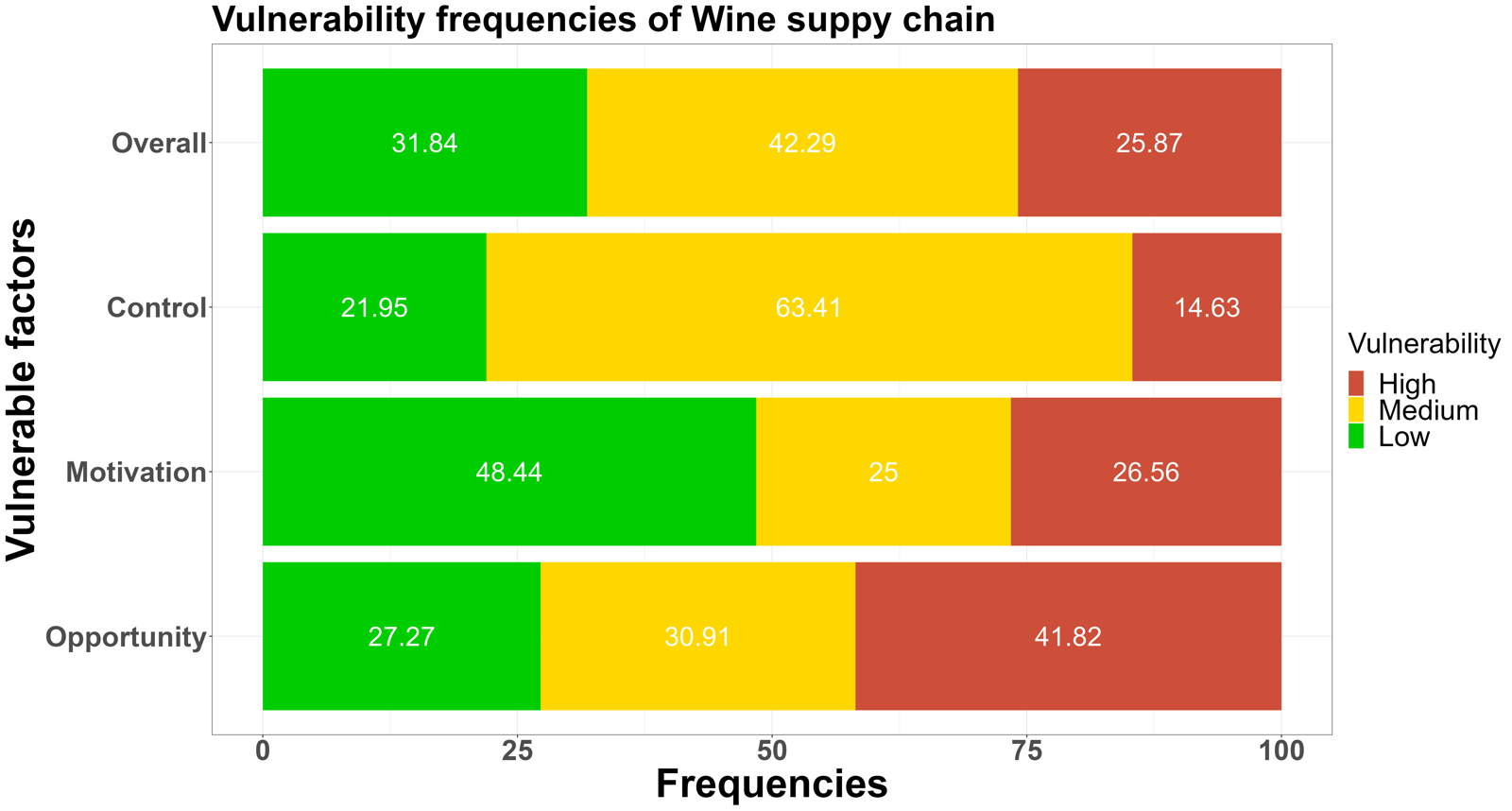
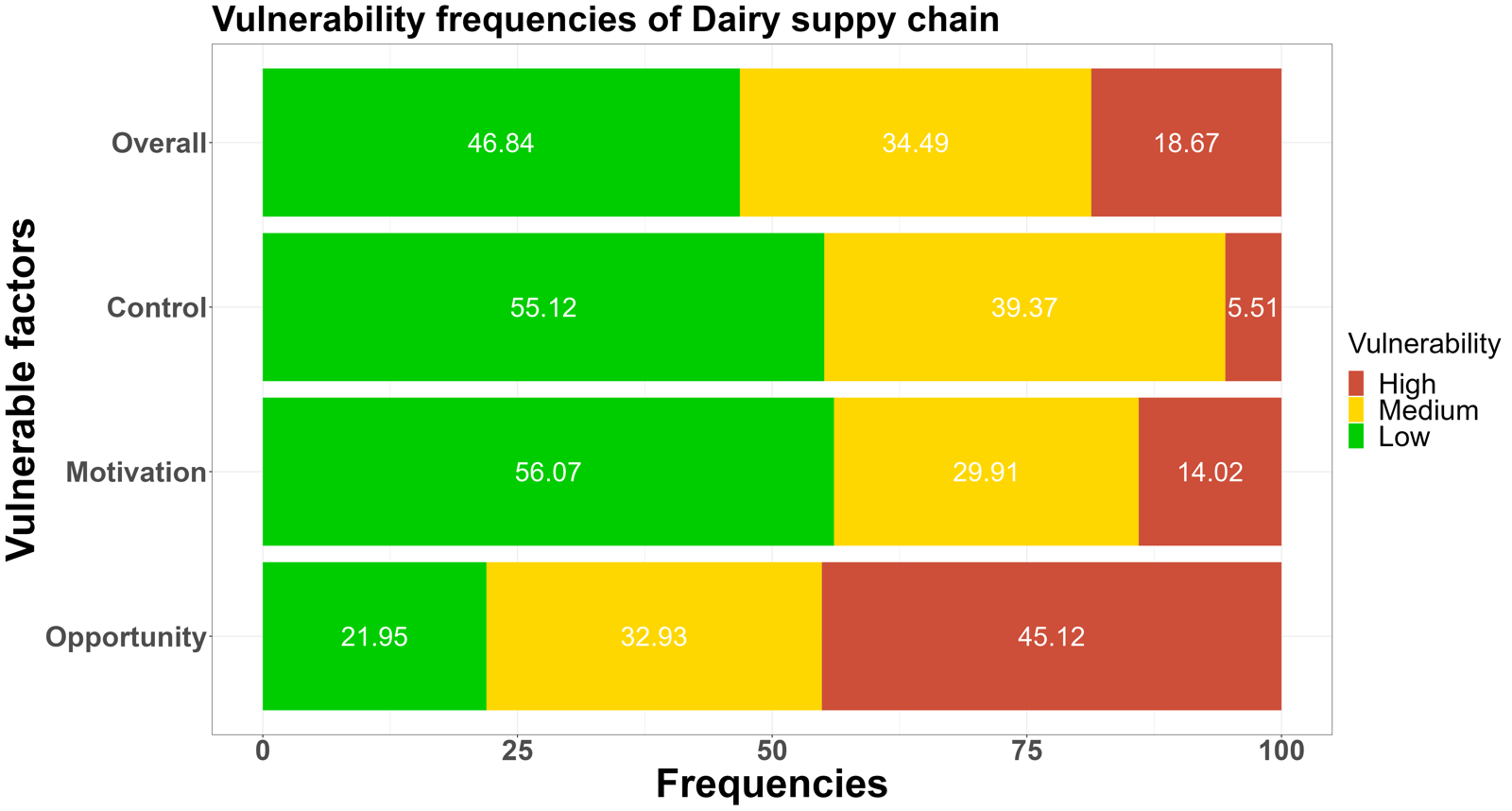
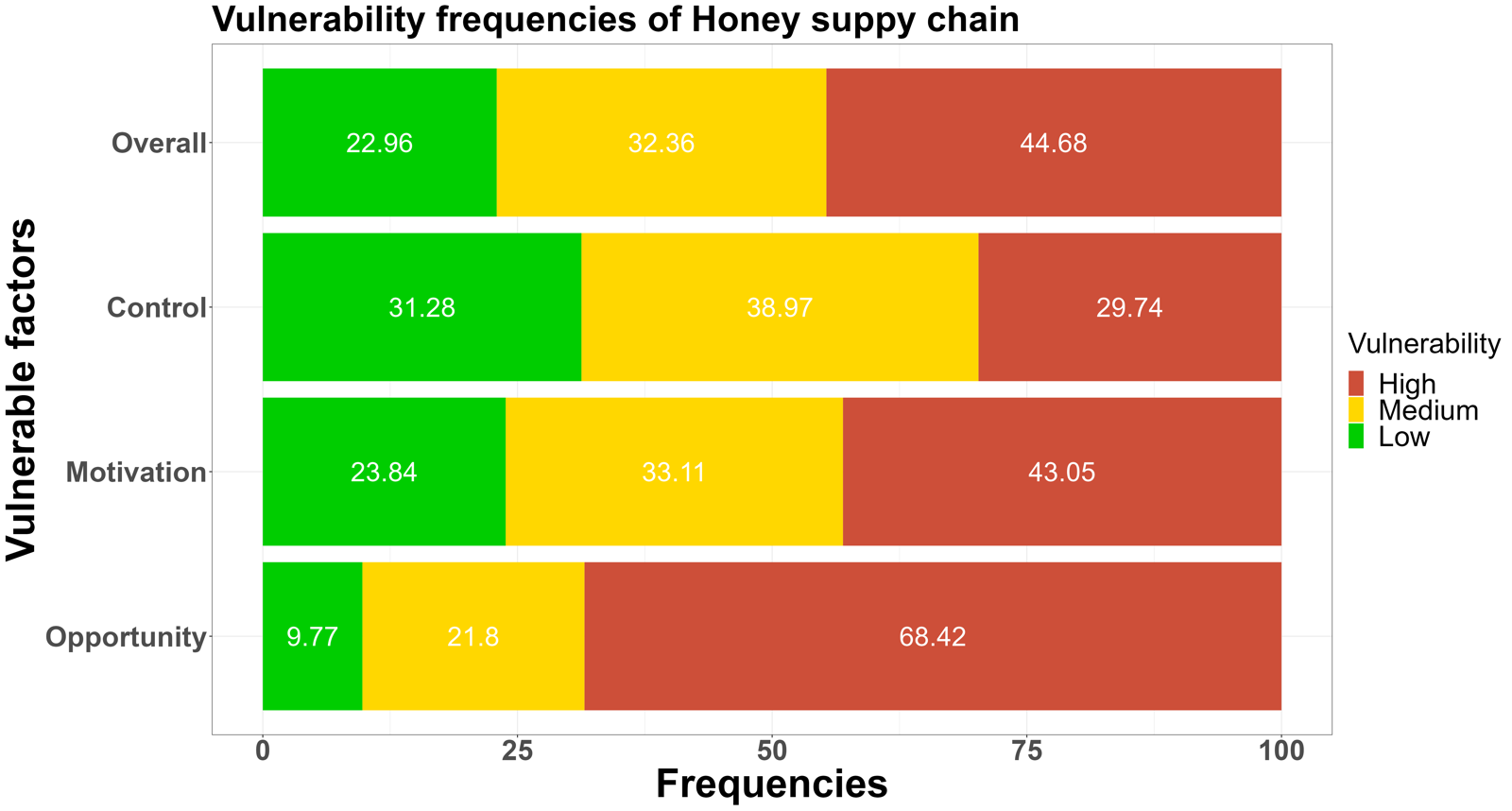
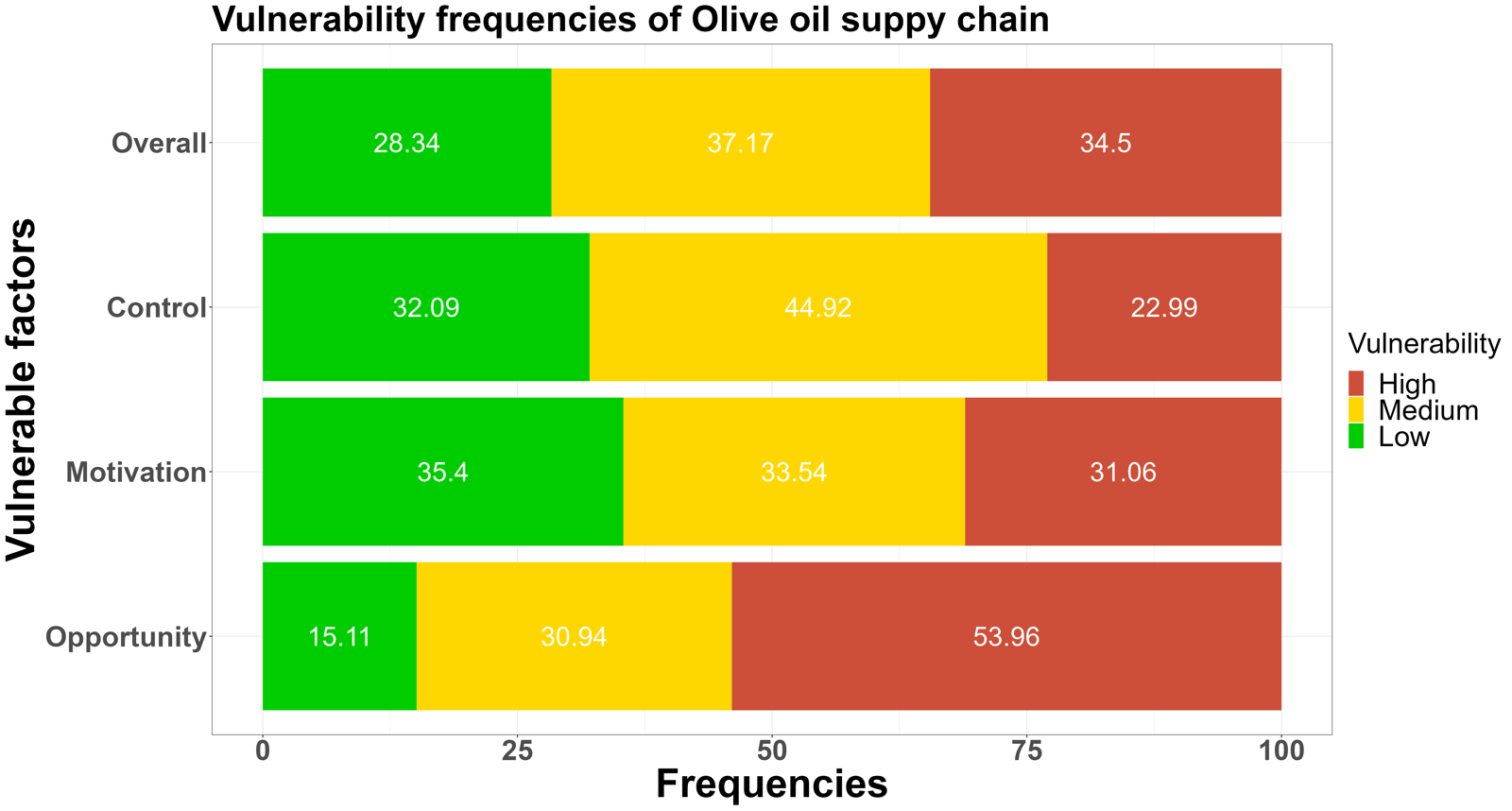
The low-medium-high vulnerability frequencies of answers of the opportunities, motivations, and control measures were shown in Figure 1.sentence permalink
The leading fraud vulnerability could be defined as a medium-high level for all seven supply chains.sentence permalink
Figure 1. The low-medium-high food fraud vulnerability frequencies among the seven supply chains for the three key elements: opportunities, motivations and control measuressentence permalink
According to the comparison of fraud vulnerability levels assessed in the cereal, dairy, fish, honey, meat, olive oil, and wine supply chain, a green color refers to a low vulnerability, orange to a medium vulnerability, and red to a high vulnerability. The more prevalent the red (high vulnerability) and orange color (medium vulnerability), the higher the perceived vulnerability.sentence permalink
Fig. 1 shows fraud vulnerability frequencies among three key elements.sentence permalink
In the overall results of food fraud vulnerability frequencies, the orange-red (medium-high vulnerability) colour dominates in the above supply chains, which means more than 50% fraud factors were rated as medium-high risk levels.sentence permalink
Among all supply chains, the honey supply chain has the highest proportion (44.88%) of high-risk factors, and only 22.96 % of all questions were rated low vulnerability.sentence permalink
In the details of key elements, the opportunities were reported most in the red color (>40%) compared with motivation and control methods.sentence permalink
Especially in the honey and olive oil supply chain, more than 50% of fraud factors were rated as high risk.sentence permalink
The fraud factors related to the Q1-5 were the main contributions, which means the which means the adulteration of olive oil and honey does not present any particular technical difficulties and, taking into account the liquid state of olive oil and honey, it can be much more easy to be substituted compared with meat and fish products.sentence permalink
Most participants rated the factors, ‘availability technology and knowledge to adulterate raw materials’, ‘detectability of adulteration in final products’, and ‘complexity of counterfeiting’ as high risk in the supply chain.sentence permalink
It supports the opinion that olive oil and honey can easily be substituted by lower-quality oil or syrup.sentence permalink
In the section on motivation, although honey and olive oil were still found to have higher fraud scores, it is worth noting that 37.62% of the fraud factors in the meat supply chain were rated as medium risk and 18.81% were rated as high risk in terms of motivation.sentence permalink
Same higher-medium risks were also reported in the fish supply chain.sentence permalink
In the detailed fraud factors, the Q9, Q10, and Q18, were rated as high risk in most of supply chains.sentence permalink
These fraud factors are related to the high premium components of agricultural products, price differences between different origins, and price differences between agricultural raw materials and final products.sentence permalink
In the section on control measures, the high fraud vulnerability in factors such as Q21, Q23, Q24, and Q26 is perceived as low-medium regarding food fraud in most of the supply chains.sentence permalink
This shows that major EU food supply chains still lack a common, trustworthy information system to provide food traceability services.sentence permalink
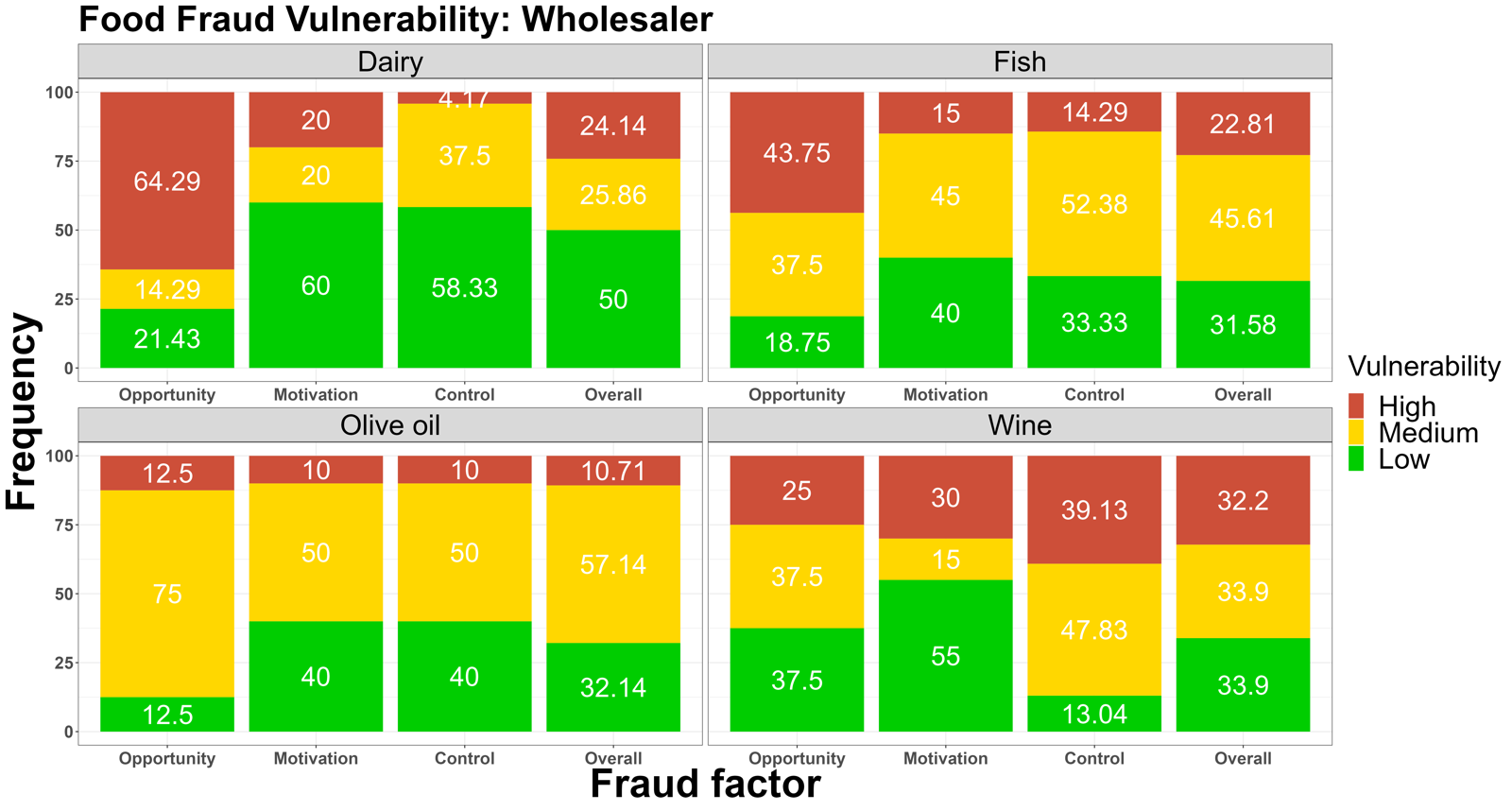
4.3 The comparison of fraud vulnerability between different stakeholders
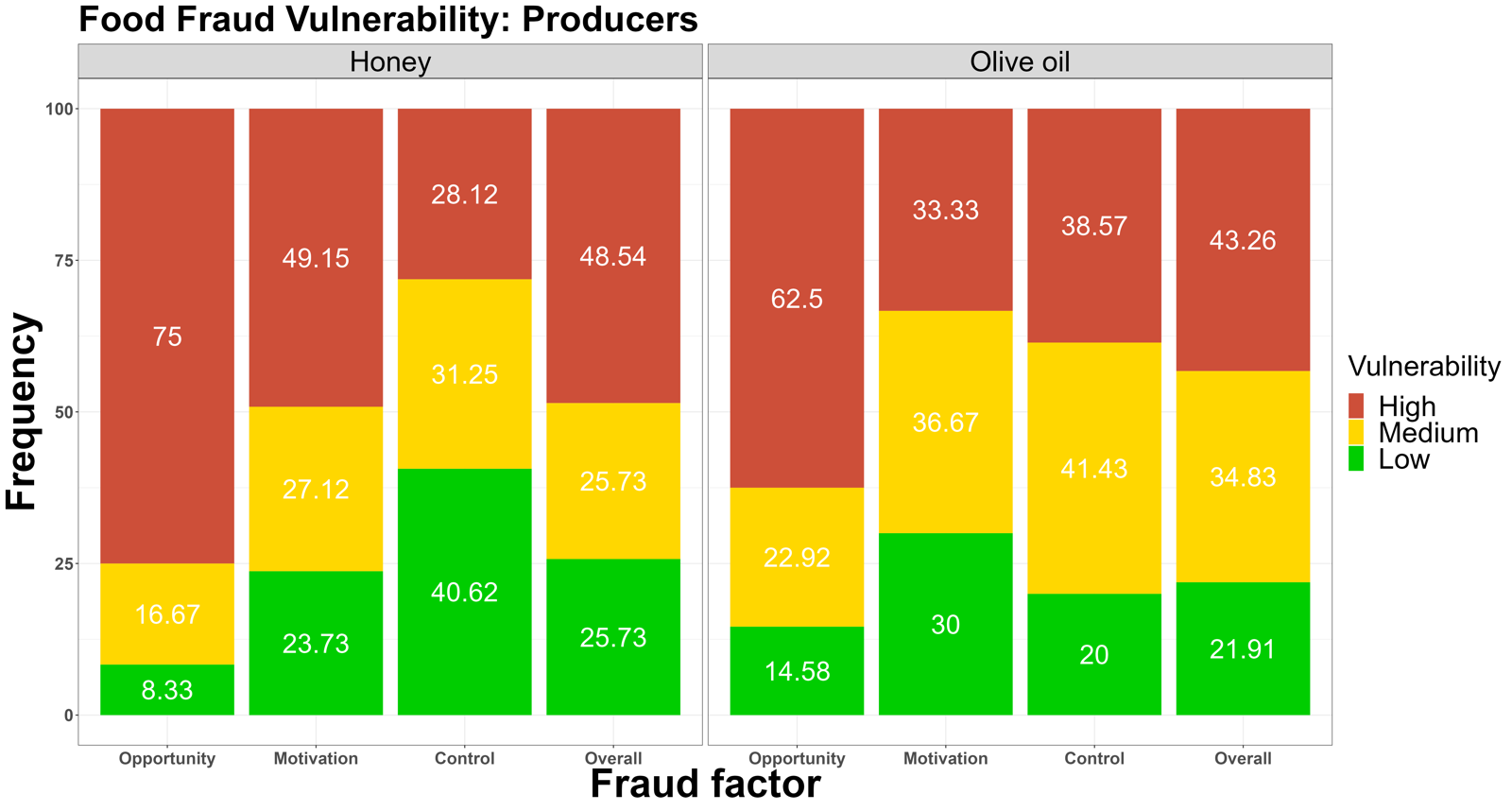
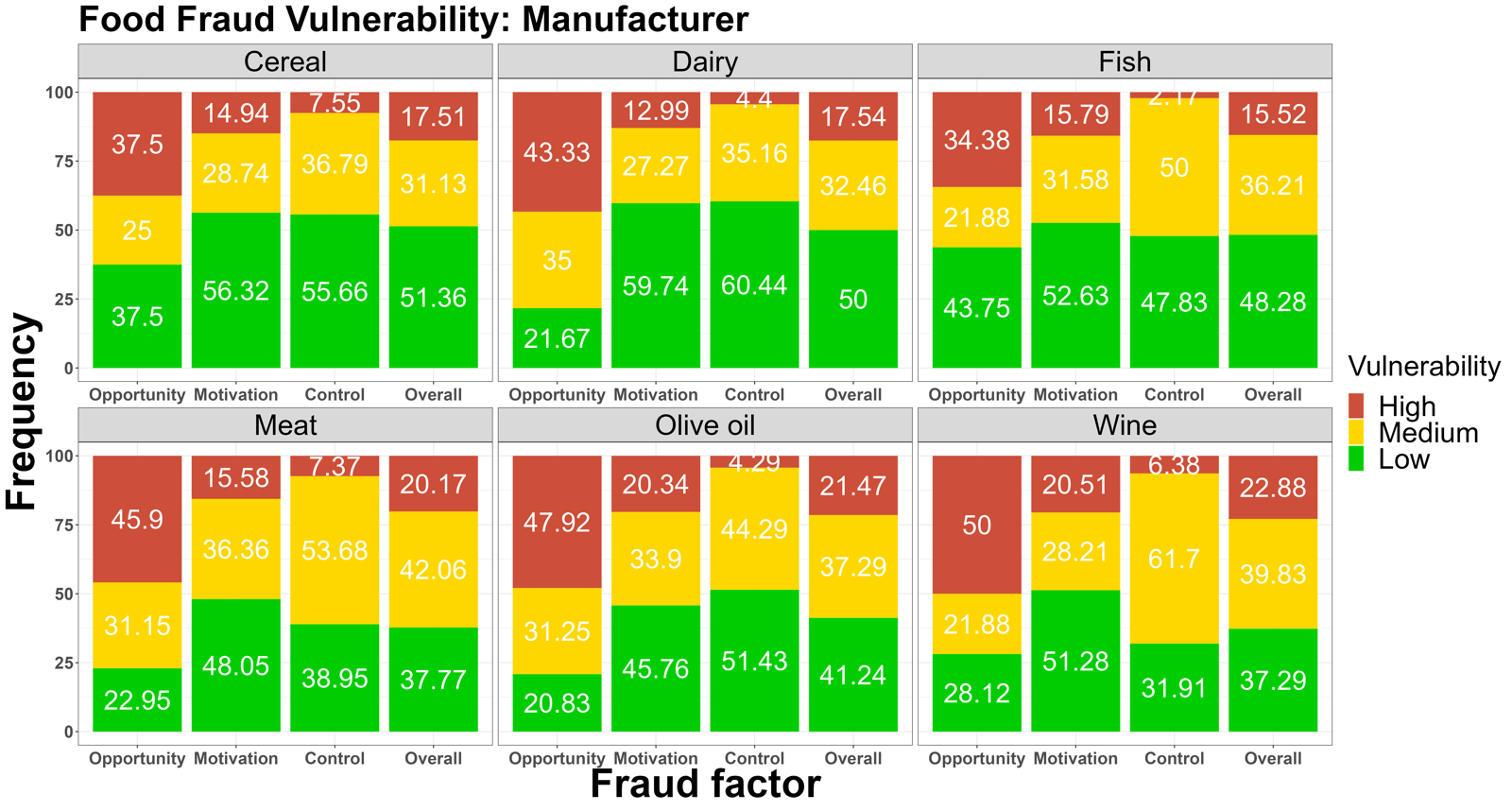
Figure 2. The low-medium-high food fraud vulnerability frequencies among the different stakeholders among the seven supply chainssentence permalink
Fig. 2 shows the differences in fraud vulnerability among stakeholders in seven supply chains.sentence permalink
The producer, manufacturer, wholesaler, and retailer are the main stakeholders participating in this assessment.sentence permalink
Due to differences in supply chain composition, not every supply chain share all the above four roles.sentence permalink
However, the vulnerability to fraud represented by these roles in different supply chains is still indicated in Fig 2.sentence permalink
For the producer, the overall fraud vulnerability in honey is higher than olive oil.sentence permalink
But for the element opportunity, the honey supply chain is reported to have a high risk of fraud at 75% of producers, which is higher than 62.5% of opportunities in the olive oil supply chain.sentence permalink
For the manufacturer's results, the supply chain cereal, dairy, fish, meat, olive oil, and wine were included in the fraud vulnerability assessment.sentence permalink
The wine manufacturer showed the highest overall fraud risks (22.88%).sentence permalink
The most vulnerable nodes were also found in opportunity and motivation.sentence permalink
The same trend was also found in the wholesaler department, that is, in the control section, most fraud points were rated as low to medium risk.sentence permalink
However, at the dealer level, all three key elements showed higher risks.sentence permalink
For example, in the fish supply chain, 85.71% of opportunity was rated as high risk, and in the olive oil supply chain, 52.63% of factors related to motivation were rated as high risk.sentence permalink
For the honey supply chain, control measures section, 47.37% factors were scored as high risk.sentence permalink
In summary, for the same stakeholders, different supply chains exhibit different vulnerabilities, which demonstrates the need to consider the special circumstances of supply chains when developing food fraud mitigation measures.sentence permalink
5. Conclusion
After conducting this food fraud vulnerability assessment, it has been found that seven supply chains have a moderate to high vulnerability risk.sentence permalink
Among these, the honey, olive oil, wine, and meat supply chains have higher risks in all three areas of opportunity, motivation, and control measures.sentence permalink
On the other hand, other supply chains, such as cereal, dairy, and fish, still have relatively consistent vulnerabilities in the opportunity and motivation areas.sentence permalink
This trend is due to the accessibility of adulteration technology, high premiums for raw materials or final products, price differences between different origins, and the competitiveness of the industry.sentence permalink
These factors pose a threat to the entire food supply chain, from producers and processors to sales.sentence permalink
At the same time, while different stakeholders may exhibit different fraud risks, overall fraud vulnerability among opportunities is higher than motivation and lack of controls.sentence permalink
The lack of regulatory systems focused on food fraud and unreliable traceability systems are two major pain points currently plaguing major EU supply chains in the area of control.sentence permalink
Therefore, the deployment of traceability systems with the help of digital technologies should be the focus of the next steps.sentence permalink
6. Future research
As per the research plan of the Watson project along with the findings of the current food fraud vulnerability assessment, we will concentrate on the following three points for further research:sentence permalink
1. We will consistently gather more vulnerability assessment questionnaires that can cover most of the supply chain stakeholders to thoroughly evaluate the food fraud issues faced by each agri-food chain;sentence permalink
2. Based on the initial conclusions on food fraud vulnerability assessment, we will develop customized food traceability systems for different supply chains. Various digital technologies such as blockchain, Internet of Things, and cloud computing will be the focal point of research;sentence permalink
3. When creating an early warning system for food fraud, it is crucial to consider the vulnerabilities of various stakeholders in the supply chain. By conducting a vulnerability assessment, we can identify the weakest links in the complex supply chain and gather relevant historical data about food fraud incidents. This information will help us to build a comprehensive early warning system that can effectively mitigate the risks associated with food fraud.sentence permalink
References
Manning, L., & Soon, J. M. (2019). Food fraud vulnerability assessment: Reliable data sources and effective assessment approaches. Trends in Food Science & Technology, 91, 159–168. https://doi.org/10.1016/j.tifs.2019.07.007sentence permalink
Ruth, S. M. van. (2019). Food Fraud and Vulnerability Assessments. Encyclopedia of Food Chemistry, 663–669. https://doi.org/10.1016/B978-0-08-100596-5.21789-7sentence permalink
Yan, J., Erasmus, S. W., Toro, M. A., Huang, H., & Ruth, S. M. van. (2020). Food fraud: Assessing fraud vulnerability in the extra virgin olive oil supply chain. Food Control, 111, 107081. https://doi.org/10.1016/J.FOODCONT.2019.107081sentence permalink